* feat: added crds for infisical provider Signed-off-by: = <akhilmhdh@gmail.com> * feat: implemented infisical provider logic Signed-off-by: = <akhilmhdh@gmail.com> * fix: resolved broken doc building due to vault doc error Signed-off-by: = <akhilmhdh@gmail.com> * docs: added doc for infisical provider Signed-off-by: = <akhilmhdh@gmail.com> * docs: fixed a warning in mkdocs on link Signed-off-by: = <akhilmhdh@gmail.com> * feat: resolved all lint issues Signed-off-by: = <akhilmhdh@gmail.com> * doc: removed k8s auth release banner from infisical doc Signed-off-by: = <akhilmhdh@gmail.com> * feat: added support for property to infisical provider Signed-off-by: = <akhilmhdh@gmail.com> * feat: removed auth type and made implicit ordering of authentication based on feedback Signed-off-by: = <akhilmhdh@gmail.com> * feat: support for referent authentication Signed-off-by: = <akhilmhdh@gmail.com> * feat: added error for tag not supported in find Signed-off-by: = <akhilmhdh@gmail.com> * fix: resolved failing build Signed-off-by: = <akhilmhdh@gmail.com> * feat: updated doc and added stability matrix for infisical Signed-off-by: = <akhilmhdh@gmail.com> * feat: switched to less error prone use and revoke token strategy and added validate interface logic Signed-off-by: = <akhilmhdh@gmail.com> * feat: code lint issue fixes Signed-off-by: = <akhilmhdh@gmail.com> * feat: resolved review comments for infisical client Signed-off-by: = <akhilmhdh@gmail.com> * feat: improved test cases and resolved sonar issues Signed-off-by: = <akhilmhdh@gmail.com> * feat: resolved sonar suggestions Signed-off-by: = <akhilmhdh@gmail.com> * feat: resolved sonar suggestions for test const ids Signed-off-by: = <akhilmhdh@gmail.com> * feat: store changes to assertError Signed-off-by: = <akhilmhdh@gmail.com> --------- Signed-off-by: = <akhilmhdh@gmail.com>
2.1 KiB
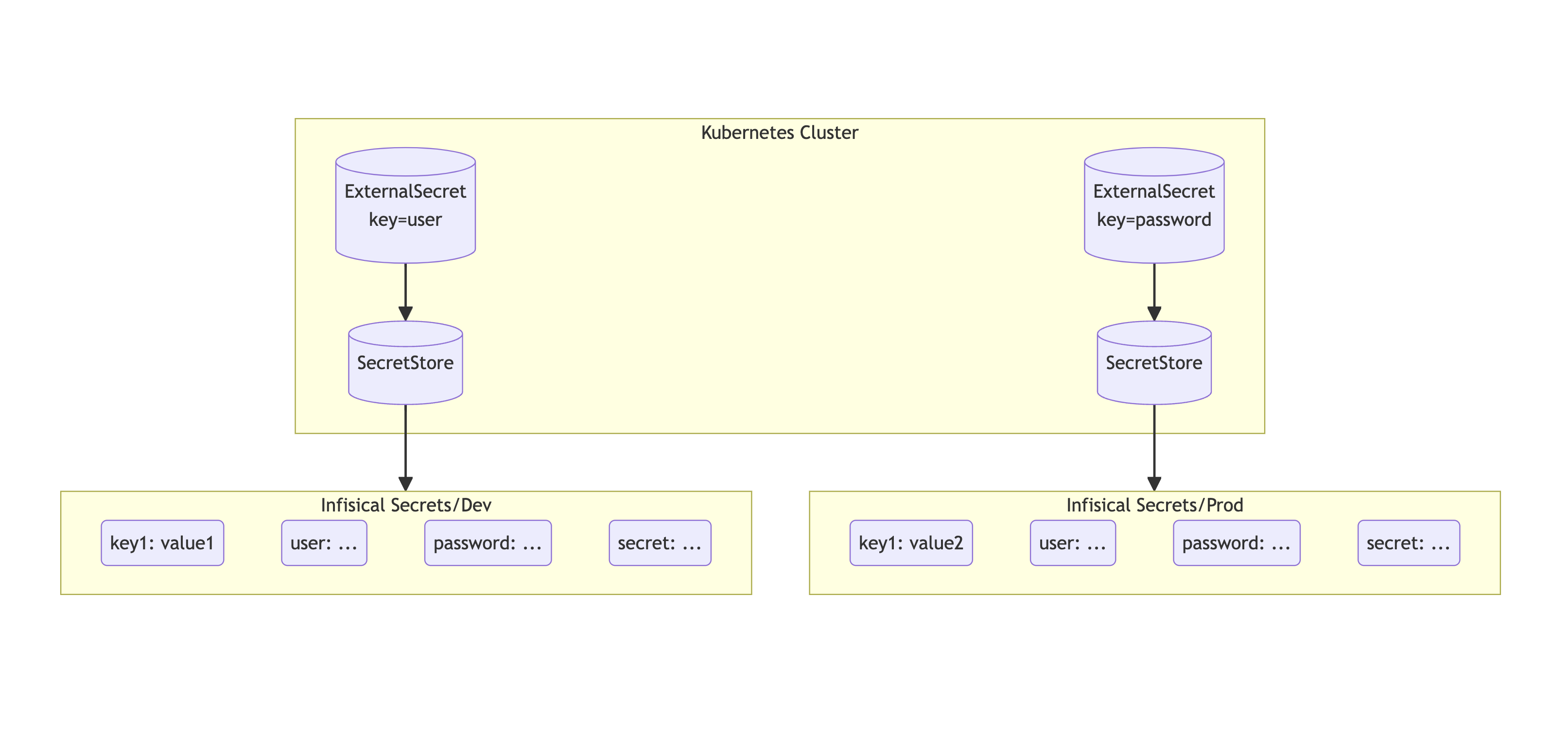
Sync secrets from Infisical to your Kubernetes cluster using External Secrets Operator.
Authentication
In order for the operator to fetch secrets from Infisical, it needs to first authenticate with Infisical.
To authenticate, you can use Universal Auth from Machine identities.
Follow the guide here to learn how to create and obtain a pair of Client Secret and Client ID.
Storing Your Machine Identity Secrets
Once you have generated a pair of Client ID and Client Secret, you will need to store these credentials in your cluster as a Kubernetes secret.
!!! note inline end Remember to replace with your own Machine Identity credentials.
apiVersion: v1
kind: Secret
metadata:
name: universal-auth-credentials
type: Opaque
stringData:
clientId: <machine identity client id>
clientSecret: <machine identity client secret>
Secret Store
You will then need to create a generic SecretStore. An sample SecretStore has been is shown below.
!!! tip inline end
To get your project slug from Infisical, head over to the project settings and click the button Copy Project Slug.
{% include 'infisical-generic-secret-store.yaml' %}
!!! Note
For ClusterSecretStore, be sure to set namespace in universalAuthCredentials.clientId and universalAuthCredentials.clientSecret.
Fetch Individual Secret(s)
To sync one or more secrets individually, use the following YAML:
{% include 'infisical-fetch-secret.yaml' %}
Fetch All Secrets
To sync all secrets from an Infisical , use the following YAML:
{% include 'infisical-fetch-all-secrets.yaml' %}
Filter By Prefix/Name
To filter secrets by path (path prefix) and name (regular expression).
{% include 'infisical-filtered-secrets.yaml' %}