3.8 KiB
IBM Cloud Secret Manager
External Secrets Operator integrates with IBM Secret Manager for secret management.
Authentication
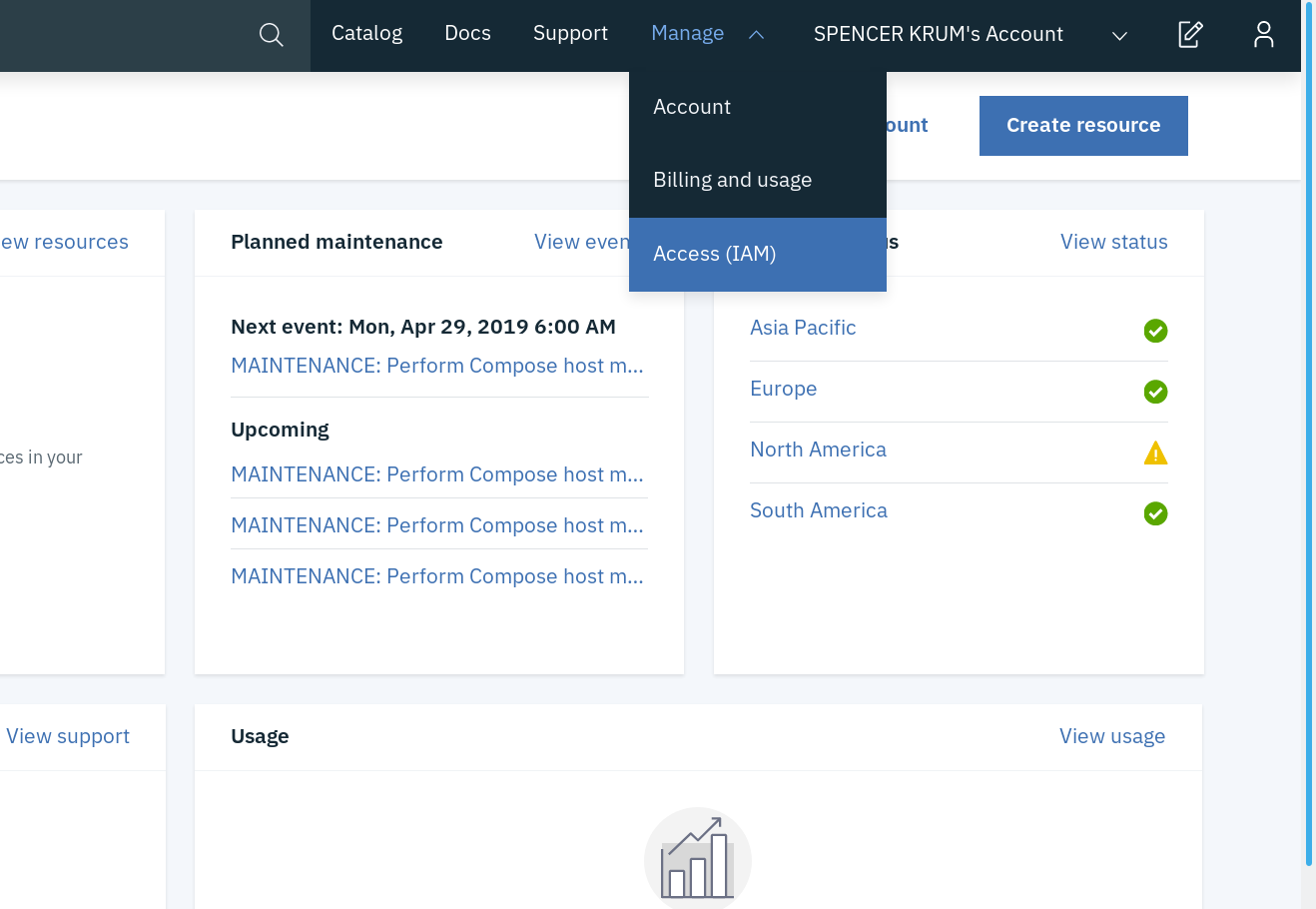
At the moment, we only support API key authentication for this provider. To generate your key (for test purposes we are going to generate from your user), first got to your (Access IAM) page:
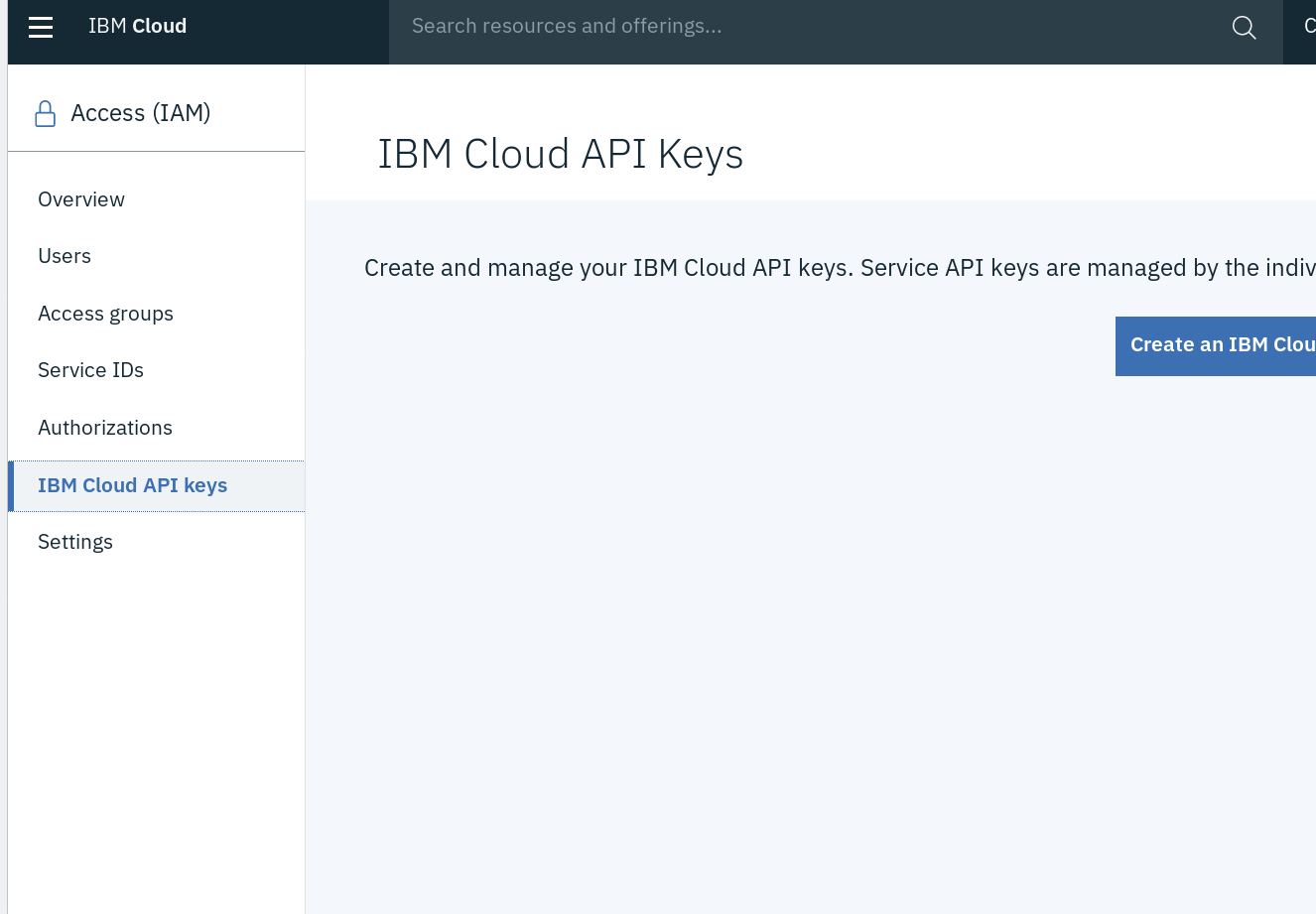
On the left, click "IBM Cloud API Keys":
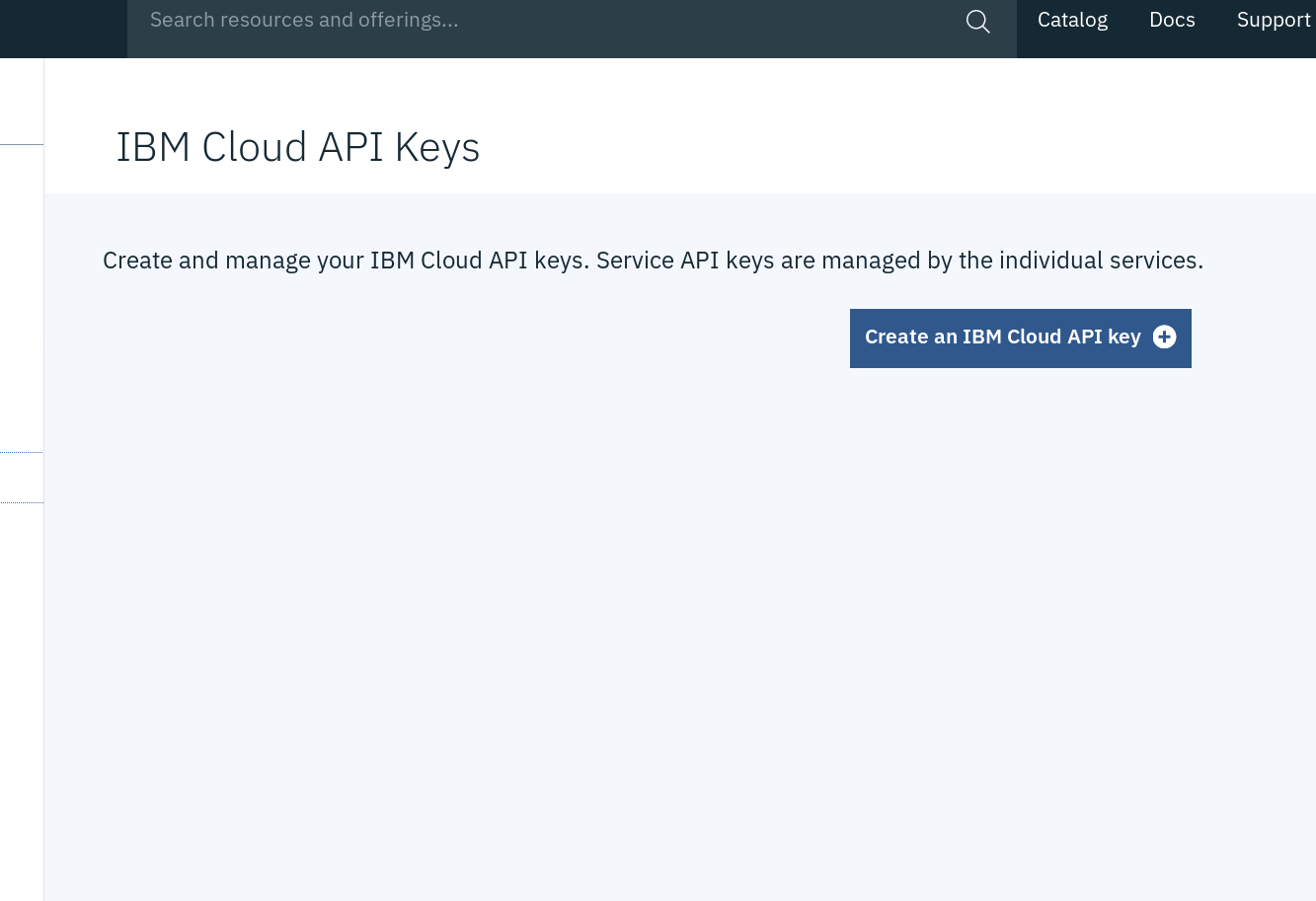
Press "Create an IBM Cloud API Key":
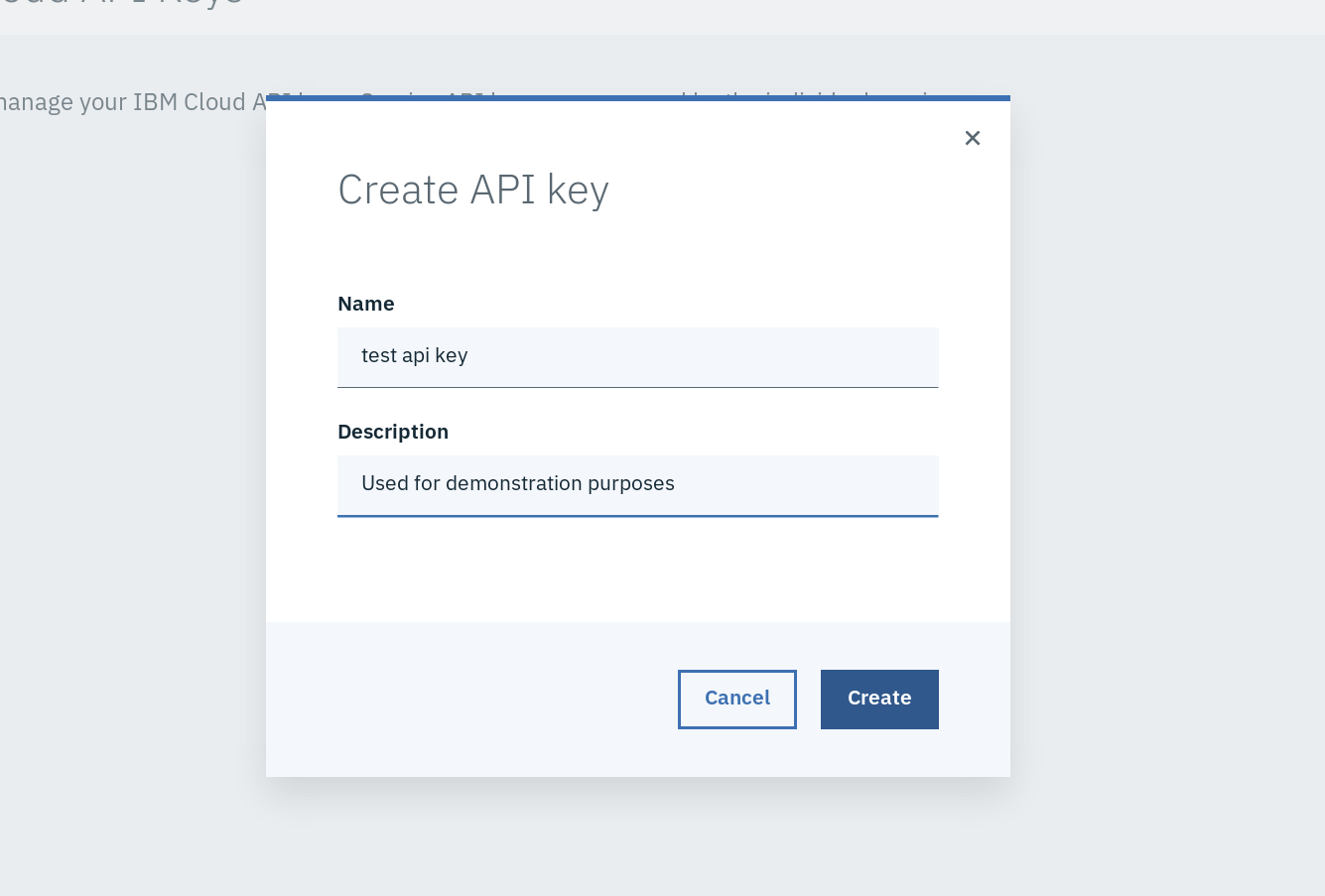
Pick a name and description for your key:
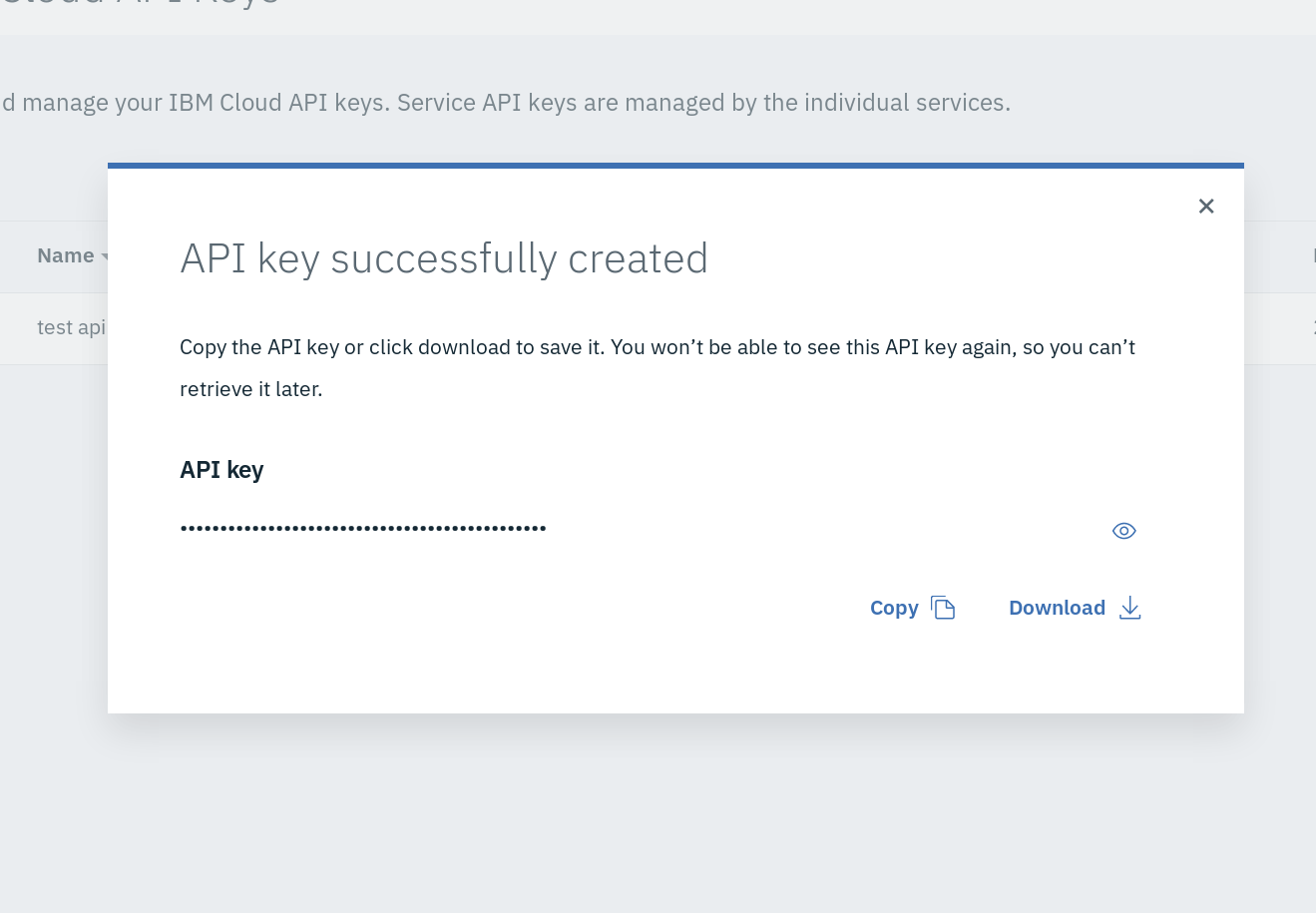
You have created a key. Press the eyeball to show the key. Copy or save it because keys can't be displayed or downloaded twice.
API key secret
Create a secret containing your apiKey:
kubectl create secret generic ibm-secret --from-literal=apiKey='API_KEY_VALUE'
Update secret store
Be sure the ibm provider is listed in the Kind=SecretStore
{% include 'ibm-secret-store.yaml' %}
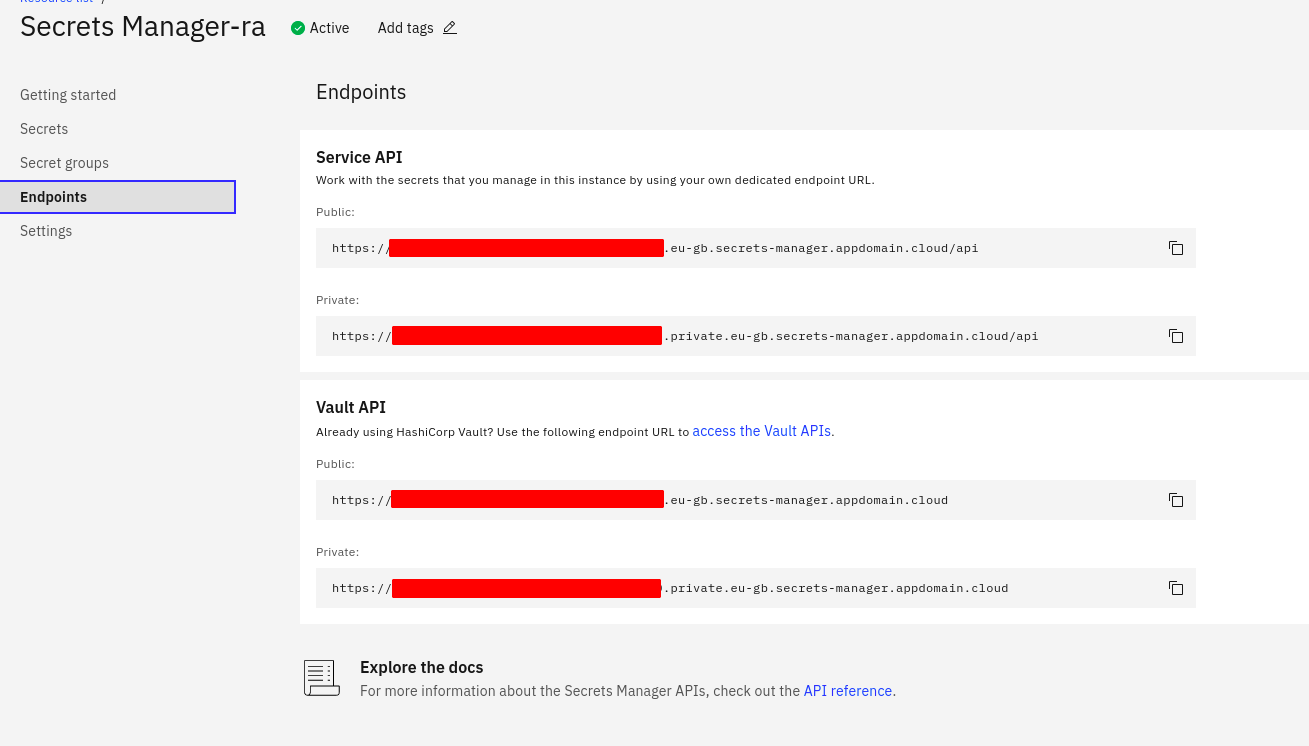
To find your serviceURL, under your Secrets Manager resource, go to "Endpoints" on the left.
Note: Use the url without the /api suffix that is presented in the UI.
See here for a list of publicly available endpoints.
Secret Types
We support all secret types of IBM Secrets Manager: arbitrary, username_password, iam_credentials and imported_cert. To define the type of secret you would like to sync you need to prefix the secret id with the desired type. If the secret type is not specified it is defaulted to arbitrary:
{% include 'ibm-es-types.yaml' %}
The behavior for the different secret types is as following:
arbitrary
remoteRefretrieves a string from secrets manager and sets it for specifiedsecretKeydataFromretrieves a string from secrets manager and tries to parse it as JSON object setting the key:values pairs in resulting Kubernetes secret if successful
username_password
remoteRefrequires apropertyto be set for eitherusernameorpasswordto retrieve respective fields from the secrets manager secret and set in specifiedsecretKeydataFromretrieves bothusernameandpasswordfields from the secrets manager secret and sets appropriate key:value pairs in the resulting Kubernetes secret
iam_credentials
remoteRefretrieves an apikey from secrets manager and sets it for specifiedsecretKeydataFromretrieves an apikey from secrets manager and sets it for theapikeyKubernetes secret key
imported_cert
remoteRefrequires apropertyto be set for eithercertificate,private_keyorintermediateto retrieve respective fields from the secrets manager secret and set in specifiedsecretKeydataFromretrieves allcertificate,private_keyandintermediatefields from the secrets manager secret and sets appropriate key:value pairs in the resulting Kubernetes secret
Creating external secret
To create a kubernetes secret from the IBM Secrets Manager, a Kind=ExternalSecret is needed.
{% include 'ibm-external-secret.yaml' %}
Currently we can only get the secret by its id and not its name, so something like 565287ce-578f-8d96-a746-9409d531fe2a.
Getting the Kubernetes secret
The operator will fetch the IBM Secret Manager secret and inject it as a Kind=Secret
kubectl get secret secret-to-be-created -n <namespace> | -o jsonpath='{.data.test}' | base64 -d