2.1 KiB
Parameter Store
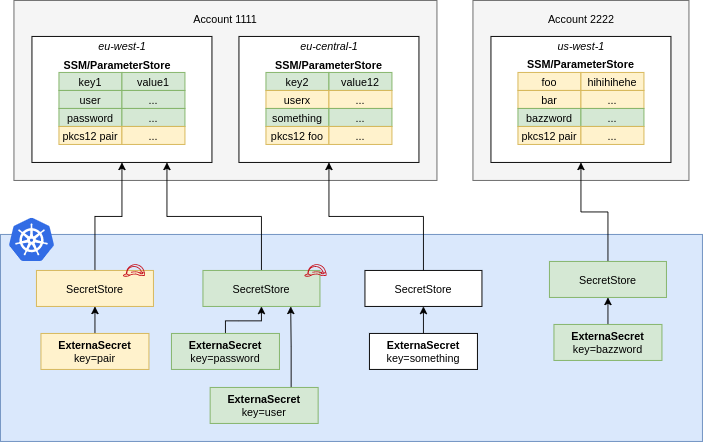
A ParameterStore points to AWS SSM Parameter Store in a certain account within a
defined region. You should define Roles that define fine-grained access to
individual secrets and pass them to ESO using spec.provider.aws.role. This
way users of the SecretStore can only access the secrets necessary.
{% include 'aws-parameter-store.yaml' %}
!!! warning "API Pricing & Throttling" The SSM Parameter Store API is charged by throughput and is available in different tiers, see pricing. Please estimate your costs before using ESO. Cost depends on the RefreshInterval of your ExternalSecrets.
IAM Policy
Create a IAM Policy to pin down access to secrets matching dev-*, for further information see AWS Documentation:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"ssm:GetParameter*"
],
"Resource": "arn:aws:ssm:us-east-2:123456789012:parameter/dev-*"
}
]
}
JSON Secret Values
You can store JSON objects in a parameter. You can access nested values or arrays using gjson syntax:
Consider the following JSON object that is stored in the Parameter Store key my-json-secret:
{
"name": {"first": "Tom", "last": "Anderson"},
"friends": [
{"first": "Dale", "last": "Murphy"},
{"first": "Roger", "last": "Craig"},
{"first": "Jane", "last": "Murphy"}
]
}
This is an example on how you would look up nested keys in the above json object:
apiVersion: external-secrets.io/v1alpha1
kind: ExternalSecret
metadata:
name: example
spec:
# [omitted for brevity]
data:
- secretKey: firstname
remoteRef:
key: my-json-secret
property: name.first # Tom
- secretKey: first_friend
remoteRef:
key: my-json-secret
property: friends.1.first # Roger
--8<-- "snippets/provider-aws-access.md"